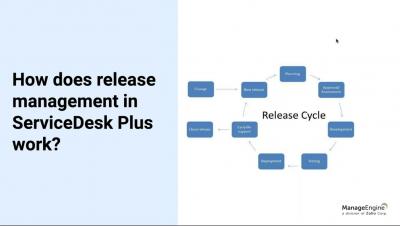
Setting the Cornerstone of a Successful ITSM Practice [Webinar]
One of the key challenges that most IT service desks face is transitioning ITSM best practices from the drawing board to daily practice. And seldom do teams realize that this hurdle can be handled effectively by leveraging the capabilities offered by #ITSM tools like ServiceDesk Plus. This session is a blend of the recommended industry best practices and ManageEngine's 15 years of ITSM experience, all aimed at helping service desk teams implement best practices in their day-to-day #ITSMprocesses.