Operations | Monitoring | ITSM | DevOps | Cloud
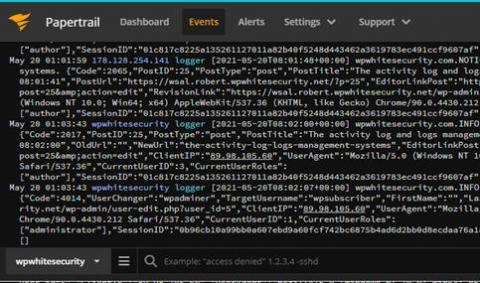
Logging
The latest News and Information on Log Management, Log Analytics and related technologies.
IT Service Intelligence (ITSI) Comes to Splunk Mobile and TV
Why should only Dashboard Studio users get all the fun new features on Splunk Mobile and Splunk TV? To spread the cheer this new year, we brought the latest and greatest Mobile and TV features to IT Service Intelligence (ITSI) Glass Tables, so that you can view your ITSI data anywhere at any time!
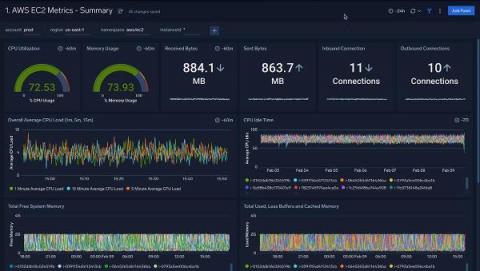
The Best Prometheus Dashboards
In this roundup of the best dashboards powered by the Prometheus metrics monitoring system, we wanted to show you some of the best use cases for this ever-popular solution for time series metrics alerting.
Optimized Traffic Mirroring Examples - Part 2
In a previous post, we looked at an example of a fictional bookstore company and recommended mirroring strategies for that specific scenario. In this post, we’ll be looking at a fictional bank and recommended mirroring strategies for their network traffic. For a list of the most commonly used strategies, check out our traffic mirroring tutorial.
Minimize the Risk of Logging Over the Internet: How LogStream Cloud Can Be Paired With Cloudflare
With the proliferation of security SaaS platforms, such as Cloudflare, Proofpoint, and PingOne, enterprises must figure out how to integrate third-party data shipped over the internet into their analytics and SIEM platforms. This requirement to integrate third-party data raises a host of security, infrastructure, and data quality questions. Enterprises can lower risk, and complete projects faster, by using Cribl LogStream Cloud to solve their challenges in managing third-party SaaS platform data.
DevOps State of Mind Episode 8: What do DevSecOps and Formula 1 have in common?
Josh Minthorne is the co-founder and global technology director of Axcelinno, an IT technology consultancy and professional services company that helps organizations define and implement their DevSecOps adoption and cloud migration. Today, we're talking about why the security landscape has made companies hesitant to move to the cloud and what they can do to migrate with confidence.
Broadcom Software Launches Cloud-Based Log Analytics Service for Data-Driven Network Visibility
Human operators utilizing traditional network monitoring software with methods like SNMP, ping, or flow tracking are still limited to diagnosis and triage issues within the four walls of the on-premise data center. But with increased adoption of cloud, SD-WAN and “work from anywhere,” application workloads are getting more distributed and creating network monitoring visibility gaps.