Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
What is Zero Trust and How IT Infrastructure Monitoring (ITIM) Makes it Happen
When the concept of Zero Trust emerged in 2010, it marked a sea change in how IT and network security are handled. The term, invented by Forrester Research analyst John Kindervag, is loosely based on the “never trust, always verify” motto. So why is this a sea change? Before 2010, IT focused on perimeter defenses and the concept of DMZs — areas of the network they deemed safe based on the protection they implemented.
What's Stopping the Adoption of Network Automation?
Is there a gap between the potential of network automation and widespread industry implementation? Phil Gervasi explores how the adoption challenges of network automation are multifaceted and aren’t all technical in nature.
Monitor More of Your IT Infrastructure
The First 48 Hours of Ransomeware Incident Response On-Demand Webinar
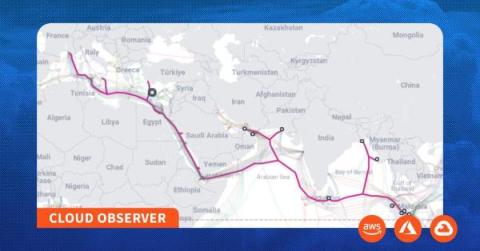
Cloud Observer: Subsea Cable Maintenance Impacts Cloud Connectivity
In this edition of the Cloud Observer, we dig into the impacts of recent submarine cable maintenance on intercontinental cloud connectivity and call for the greater transparency from the submarine cable industry about incidents which cause critical cables to be taken out of service.
Practical Demo: Elevate Your VPN. Empower Your Hybrid Workforce
On-premise vs SaaS: Which Network Monitoring Tool You Should Choose?
On-premise or SaaS network monitoring tool: which one to choose? This question has been bugging many businesses for quite a few years now. And no matter how much I hate to say it but the answer to this burning question is — it depends. Yes, it depends on several factors. In this blog, we will list all those factors that you should keep in mind before making this decision.
What is a Console Connect Edge Port?
What is Zero Trust and How IT Infrastructure Monitoring (ITIM) Makes it Happen
When the concept of Zero Trust emerged in 2010, it marked a sea change in how IT and network security are handled. The term, invented by Forrester Research analyst John Kindervag, is loosely based on the “never trust, always verify” motto. So why is this a sea change? Before 2010, IT focused on perimeter defenses and the concept of DMZs — areas of the network they deemed safe based on the protection they implemented.