Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
Monitoring TLS Network Traffic for Non-FIPS Compliant Cipher Suites
FIPS compliant cipher suites hold the U.S. government's seal of approval, guaranteeing their suitability for federal systems. On the other hand, non-FIPS compliant cipher suites may present security vulnerabilities due to outdated cryptographic algorithms and potential lack of perfect forward secrecy. As a result, it becomes paramount to monitor TLS network traffic for non-FIPS compliant cipher suites.
Take Your Pick! The Best Server Monitoring Tools on the Market
IT professionals are always presented with myriad solutions when seeking additional software for their network infrastructure. When it comes to server monitoring solutions, there are multiple options available. After all, every organization has its own needs, individual infrastructure and software requirements. With that in mind, the following list is a guide to help IT professionals select what they believe may be the best possible server monitoring solution for their organization.
Box and Kentik: A Google Cloud Migration Success Story
Tools and partners can make or break the cloud migration process. Read how Box used Kentik to make their Google Cloud migration successful.
Connect Over Coffee | Cross-Cloud with Megaport Cloud Router (MCR)
How to Centralize and Automate Your Network Device Configuration Management
The Importance of ICMP in Today's Digital Landscape
In today’s interconnected world, where network performance is crucial for business operations, understanding the significance of ICMP (Internet Control Message Protocol) becomes paramount. Today’s post sheds some light on the critical role of ICMP and why it should not be disabled despite legacy security concerns. By implementing proper security measures, businesses can leverage the benefits of ICMP while mitigating potential risks.
Comparing Your Multicloud Connectivity Options
As multicloud adoption surges, so too do the choices for connecting to your clouds. We break down the key solutions and their benefits.
5 Best Network Vulnerability Scanners
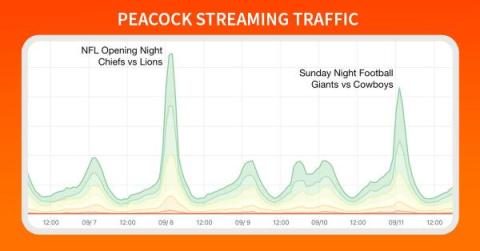
Anatomy of an OTT Traffic Surge: NFL Kickoff on Peacock
Football is officially back, and Doug Madory is here to show you exactly how well the NFL’s streaming traffic was delivered.