Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
CDN Provider Performance Monitoring: Best CDNs in the UK
This blog continues our best CDN series. Today we will be analyzing content delivery network performance and uptime in the United Kingdom over the last seven and 30 days. Tip: Are you new to CDNs? Visit our What is a CDN resource to learn more.
4 steps to bring network observability into your organization
The vast majority of corporate IT departments have a network monitoring solution. Typically that solution is built on standalone software platforms. If that’s you, this post is for you. You’re probably hearing a lot about “observability” these days. Generally, that’s the ability to answer any question and explore unknown or unexpected problems to deliver great digital experiences to your users.
Optimizing Microsoft Teams PSTN for the Hybrid Workforce
Network Monitoring Safety Checklist-5 Steps to Take
Network monitoring is a vital part of your security architecture and layered security portfolio. Step one in your network monitoring safety checklist is making sure you have network monitoring in the first place. The rest of our steps assume you have network monitoring and lay out five ways to optimize its value.
The Great Resignation - What's at Stake for IT?
Roughly 47.4 million people quit their jobs and left the workforce last year in search of better ones, leading to what we now call the Great Resignation. Then, as the economy re-opened and companies intensified hiring efforts, millions of people switched careers, searching for better working conditions and higher salaries. Experts say the trend will continue as the Gen Z population reshapes the labor market.
How To Configure Flowmon and WhatsUp Gold
In the previous “Flowmon and WhatsUp Gold: Discover application experience issues through single pane of glass” blog post we have demonstrated how IT Infrastructure Monitoring (WhatsUp Gold) and Network Performance Monitoring & Diagnostics (Flowmon) work seamlessly together to report on application performance, user experience and infrastructure status.
Peering, edge computing, and community with Grant Kirkwood | Network AF Episode 16
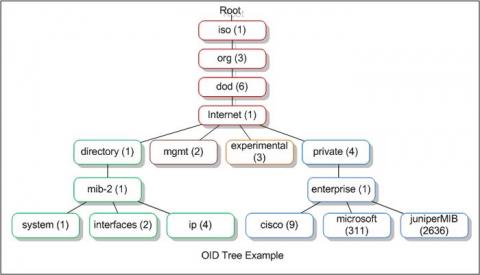
Introducing OID Monitor History
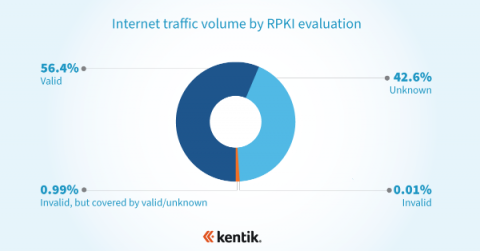
Measuring RPKI ROV adoption with NetFlow
Resource Public Key Infrastructure (RPKI) is a routing security framework that provides a mechanism for validating the correct originating autonomous system (AS) and prefix length of a BGP route. Route Origin Authorization (ROA) is a cryptographically signed object within the RPKI that asserts the correct originating AS and prefix length of a BGP route. For as long as the internet has existed, the challenge of securing its underlying protocols has persisted.