Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
How To Find A Good And Affordable Edge Protection Supplier
The Ransomware Pandemic | Security Insights Podcast: Ep. 2
Automotive consortiums: Setting new standards for safety and cybersecurity
Canonical strongly believes that the future of automotive will rely on open source to define and run the next generation of vehicles. To drive this transition, state-of-the-art cybersecurity and functional safety are critical. To learn more about the industry’s specific constraints, we are actively involved in several automotive consortiums and are contributing to automotive-related standards.
Avoid kubernetes security risks with hardening best practices
3 Effective Tips for Cloud-Native Compliance
Using RapidSpike to Support PCI DSS 4.0 Compliance
The latest version of the PCI DSS (Payment Card Industry Data Security Standard) is version 4. We are currently in the transition period following the publication of the new standard, heading towards full implementation.
How RapidSpike Cookie Monitoring Can Support Managing GDPR
When the General Data Protection Regulations (GDPR) and ePrivacy Directive (EPD) updated we saw a proliferation of “cookie consent” banners crop up on websites as a direct result. The key parts of the GDPR relating to this change are from Recital 30: Natural persons may be associated with online identifiers provided by their devices, applications, tools and protocols, such as internet protocol addresses, cookie identifiers or other identifiers such as radio frequency identification tags.
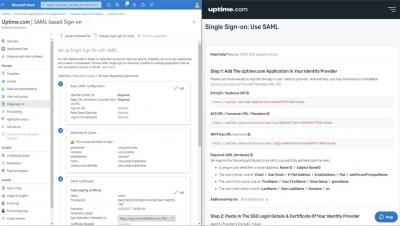
Configuring Single Sign-On (SSO) for Uptime.com
Check out our free trial, no credit card required: https://uptime.com/go/home
#monitoring, #saas, #downtime, #uptime, #nomore404, #outage, #enterprisesbusiness