Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Why Data Backup is Critical for Every Business
Reducing Security Incidents: Implementing Docker Image Security Scanner
Are you utilizing Docker to deploy your applications? If so, you're not alone. The use of Docker has skyrocketed in popularity in recent years. While it offers numerous benefits, it also introduces new security risks that need to be addressed. But, why is reducing security incidents so important? Simple - the cost of a security breach can be devastating. From lost customer trust to financial losses, the consequences of a security incident can be severe. That's why it's crucial to take steps to prevent them from occurring in the first place. Enter Docker image security scanners.
Confidential K8s Control Plane - Securing Kubernetes API with Intel SGX
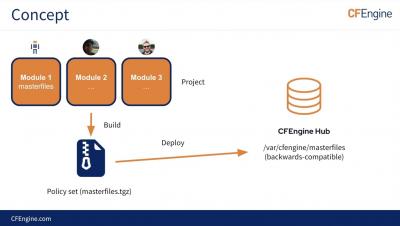
Introduction to CFEngine Build - Lars Erik Wik & Ole Herman S. Elgesem (CfgMgmtCamp 2023)
For slides and more information, see our blog post:
https://cfengine.com/blog/2023/cfgmgmtcamp/
What's new in Calico Enterprise 3.16: Egress gateway on AKS, Service Graph optimizations, and more!
We are excited to announce the early preview of Calico Enterprise 3.16. This latest release extends the active security platform’s support for egress access controls, improves the usability of network-based threat defense features, and scales visualization of Kubernetes workloads to 100s of namespaces. Let’s go through some of the highlights of this release.
Enabling TLS on a Cribl Leader Node: Step-by-Step Guide
Securing your internal systems with TLS can be a daunting task, even for experienced administrators. However, with the right tools and guidance, the process can be made more manageable. In this blog, we’ll show you how to enable TLS for your internal systems on your Cribl Leader Node. We’ll walk you through the steps, and provide a video tutorial embedded below to help you follow along.