In a World of Managing Risk, Do You Have Shiny Tech Syndrome?
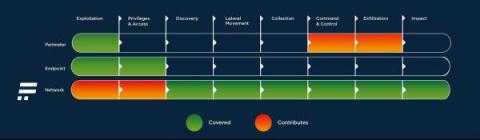
There is always something new on the horizon when it comes to technology. Isn’t it human nature to want to wait for the next 'new' model car, the next 'bigger' TV or the next 'faster' smart phone? The newest release might be more appealing – especially to higher-ups, who want the latest and greatest trending technology. But there are hidden risks associated with waiting to implement a new tool or solution.