Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Catchpoint Achieves ISO/IEC 27001:2013 Certification
7 Cybersecurity Statistics Every SMB and MSP Needs to Know in 2022
Cybersecurity isn’t just at the top of the discussion queue within the IT channel. Businesses and governments worldwide have turned a sharp eye toward rising cyber threats. Many have learned the hard way that small businesses are frequent targets of cyberattacks. The idea of “targeting a victim” itself has come into question, and more realize that widespread, indiscriminate attacks are the status quo.
Spring4Shell and the future of zero-day threats
When zero-day vulnerabilities are discovered, Cisco Secure Application can help deliver the visibility and threat detection your applications need to thwart an attack.
CFEngine: The Agent Is In 12 - Spacemacs For CFEngine
How B2B Brands Can Protect Critical Business Information Through Cybersecurity
Is it DDOS or is it you?
Server load can tell you a lot about your day-to-day user traffic. A sudden spike in server traffic can indicate an attack, but that’s not always the case. As website and performance monitoring become more mainstream, and you add a wider variety of backend testing and web monitoring checks to your infrastructure – you have to ask the question – Is that spike in server traffic DDOS? Or is it me…
Automated Threat Hunting: A Closer Look
Proactively finding and eliminating advanced threats through threat hunting is a growing necessity for many organizations, yet few have enough resources or skilled employees to do it effectively. For those who do have an active threat hunting program, the process is often manual and time consuming. With cloud security automation, however, you can implement rules that automatically adjust your security policies based on the latest threat data.
What Are The Different Types of Authentication?
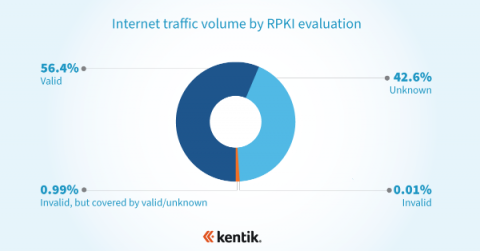
Measuring RPKI ROV adoption with NetFlow
Resource Public Key Infrastructure (RPKI) is a routing security framework that provides a mechanism for validating the correct originating autonomous system (AS) and prefix length of a BGP route. Route Origin Authorization (ROA) is a cryptographically signed object within the RPKI that asserts the correct originating AS and prefix length of a BGP route. For as long as the internet has existed, the challenge of securing its underlying protocols has persisted.