Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
Malicious threats to your website that you don't know about
The 9th February marks Safer Internet Day; a day to recognize the dangers of the internet and the need to be kinder online. But it’s not just each other we have to fear on the internet. You’ve probably heard the talk – online hackers finding their way into your website without you knowing. Spambots corrupting your Google Analytics website data. Online viruses bringing your whole website to its knees. But this is just 1% of the threats that your website faces on a daily basis.
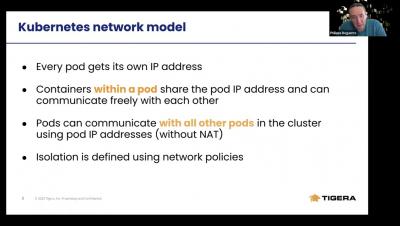
Delivering Container Security in Complex Kubernetes Environments
You may have noticed the VMware Tanzu team talking and writing a lot about container security lately, which is no accident. As DevOps and Kubernetes adoption continue their exponential growth in the enterprise, securing container workloads consistently is among the most difficult challenges associated with that transformation. There is a term we have been seeing—and using—a lot lately that encompasses a new way of looking at container security for Kubernetes: DevSecOps.
Best Practices for Writing Secure Java Code
Every Java developer should follow coding standards and best practices to develop secure Java code. It is critical your code is not vulnerable to exploits or malicious attacks. In recent times, even big organizations like eBay, the CIA, and the IRS have fallen victim to vulnerabilities in their applications that have been discovered and exploited by attackers. The following guidelines provide a solid foundation for writing secure Java code and applications.
What's New in SolarWinds Security Products
Troubleshooting microservices on K8S
Secure by Design | Our Plan for a Safer SolarWinds and Customer Community
What Is Network Security?
Cisco AppDynamics Delivers Industry-First Solution for Strengthening Security Posture Against Threats While Achieving Peak Application Performance
RapidSpike Security Headers
A few lines of code in your website’s header can make or break your security and your customer’s trust. We know how important that is to you, so at RapidSpike we’re here to empower you with data, protecting your website from the top down, and today we’re talking about the very top — your homepage header and its precious metadata.