Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
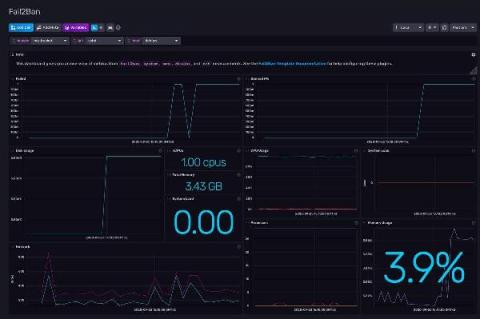
Fail2ban Monitoring with InfluxDB and Telegraf
If you have a server open to the internet on Port 22 (the default port for SSH servers), it’s common to find several “Failed password” in your auth.log (log file) every minute, due to bots constantly browsing the internet for servers that are easy to hack with common passwords. But if your auth.log is growing very fast and SSH daemon randomly refuses to create new connections, then someone probably marked your server as a target for coordinated SSH brute-force attack.
What's new in Sysdig - January 2021
Welcome to another monthly update on what’s new from Sysdig. Our team continues to work hard to bring great new features to all of our customers, automatically and for free!
Learn how to comply now before your next audit
Are you struggling to keep up with manual compliance across your infrastructure? In this 25-minute episode of the Pulling the Strings podcast, powered by Puppet, learn how Puppet Comply makes automating your configuration compliance easy -- with full view dashboards and the ability to assess, remediate and enforce all through the Puppet Enterprise solution. Listen in and discover:
How to set AWS S3 Bucket Read Permissions with Relay
Cloud environments are susceptible to security issues. A big contributor is misconfigured resources. Misconfigured S3 buckets are one example of a security risk that could expose your organization’s sensitive data to bad actors. Policies and regular enforcement of best practices are key to reducing this security risk. However, manually checking and enforcing security is time-consuming and can fall behind with all the demands a busy DevOps team faces every day.
How to export and import Timelines and templates from Elastic Security
When performing critical security investigations and threat hunts using Elastic Security, the Timeline feature is always by your side as a workspace for investigations and threat hunting. Drilling down into an event is as simple as dragging and dropping to create the query you need to investigate an alert or event.
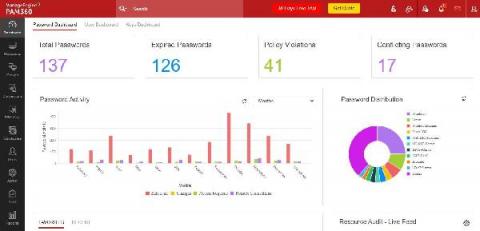
Why ManageEngine PAM360 is the ultimate privileged access management solution
At ManageEngine, we‘re building one of the most comprehensive and tightly integrated IT management software suites on the market. We have over 90 products and free tools to manage all your IT needs, including Active Directory management, help desk management, desktop and mobile device management, network and server management, application management, IT security, and analytics.
Secure Your Endpoints with Sophos & Logz.io
Intercept X is Sophos’ endpoint security solution, including anti-ransomware, zero-day exploit prevention, plus managed endpoint defense and response. It employs a layered approach reliant on multiple security techniques for endpoint detection and response (EDR). Those tactics include app lockdown, data loss prevention, web control and malware detection.
What the new WhatsApp Privacy Policy is all about and what it means for you
It was January 2007 when Steve Jobs officially announced the 1st Generation iPhone. At the time, there’s no doubt that he foresaw how the newly created concept of smartphone applications would become part of our everyday life. Fast forward a decade and we now have apps for literally everything, from trackable maps to online shopping, online banking to instant messaging.
Five worthy reads: Supply chain cyberwarfare
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week we are exploring the concept of supply chain cybersecurity in a time when there is a rising number of third-party cyberattacks.