Operations | Monitoring | ITSM | DevOps | Cloud
%term
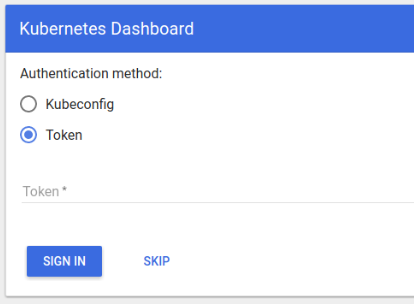
CVE-2018-18264 Privilege escalation through Kubernetes dashboard
A recently disclosed vulnerability in Kubernetes dashboard (CVE-2018-18264) exposes secrets to unauthenticated users. In this blog post we’ll explore some key takeaways regarding monitoring privilege escalation on Kubernetes.
2019's most Noteworthy Tech Conferences
It’s that time of year again–the temperature is dropping, snow is falling, and a new year has arrived. On the bright side, the end of 2018 brings the beginning of 2019 and a whole new list of tech conferences to look forward to.
New Feature - Google Hangouts Chat Notifications
Uptime Robot is already integrated with the major team communication apps and here is another addition: Google Hangouts Chat.
BigPanda Year End 2018
xFlow for Support Analysts
The Competitive Advantage Of Teamwork
Have you ever worked on a team where it was a challenge to give constructive feedback or confidently share ideas? At PagerDuty Summit 2018, Patrick Lencioni, author of The Five Dysfunctions of a Team,1 spoke about the importance of encouraging a culture of teamwork, and the role trust and vulnerability play in creating that culture.
Sumo Logic Experts Reveal Their Top Enterprise Tech and Security Predictions for 2019
We finally made it to another new year, and that means it’s time to reflect on the learnings from the previous year while also preparing for many new opportunities and challenges ahead. The enterprise tech and security industry didn’t seem to slow in 2018, so there’s no reason we would expect 2019 to be any different. So what will those “hot button” topics be this year?
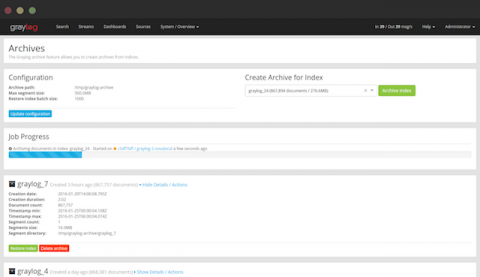
How Graylog's Advanced Functionalities Help You Make Sense of All Your Data
The inherent limitations of most log managers and the need to work within the constraints of your current hardware may force your enterprise to make some hard choices. Less useful data may be left unchecked, old information will eventually get deleted, and the amount of data that is accessed in real-time is sacrificed to reduce excess workload.
What is SIEM?
The impact of the colossal Starwood Hotels & Resorts data breach continues to reverberate across the global technology community. In its wake, the importance of log management and security information event management (SIEM) systems has once again come to the forefront. Let’s explore what SIEM is, the many acronyms emerging in the SIEM space and where logging fits into the picture.