Operations | Monitoring | ITSM | DevOps | Cloud
Incident Response
MTBF MTTR MTTF MTTA - Your guide to incident response metrics
The Debrief: Making incidents less painful with Kerim Satirli of HashiCorp & Lawrence Jones of incident.io
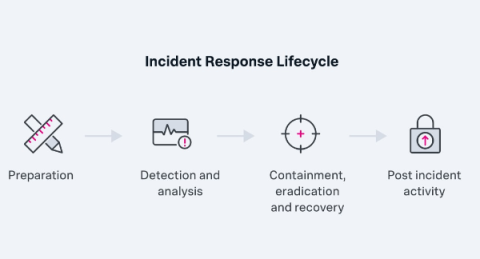
What is incident response?
The revolution in critical incident response at Dock: efficient integration and service improvement
The First 48 Hours of Ransomware Incident Response
Incident Response Plans: The Complete Guide To Creating & Maintaining IRPs
Incident response that's fast and cost-effective: Why 3 companies chose Grafana Cloud
When an incident occurs, every second counts. On-call staff need to quickly get all the relevant information in front of them in a way that’s easy to digest so they can more successfully investigate the issue and communicate with relevant stakeholders.
Incident response that's fast and cost-effective: Why these 3 companies chose Grafana Cloud
When an incident occurs, every second counts. On-call staff need to quickly get all the relevant information in front of them in a way that’s easy to digest so they can more successfully investigate the issue and communicate with relevant stakeholders.
What Is an Incident Response Team?
The vast number of threats lately lurking in cyberspace means that for cybersecurity teams, it's not a question of if an incident will occur but when. Whether it's a service outage, a data breach, a ransomware attack, or some other disturbance, organizations are bound to face security incidents eventually — the only question is if they're prepared.