Operations | Monitoring | ITSM | DevOps | Cloud
Automation
How to Detect Ransomware: 12 Monitoring & Alerting Opportunities to Automate
Ransomware threatens the loss of crucial data as well as financial loss. However, with the right knowledge and tools, you can take action to protect your business from the damaging effects of ransomware. In a 2022 Coveware Q1 ransomware report, the average ransom payment was $211,529 with an average of 26 days for downtime suffered. Ransomware obviously continues to be a huge and costly threat to industries across the board.
What to Automate First in Your SOC - Intro to Torq Webinar
Puppet and Government: Adopting infrastructure as code
Government agencies are facing a rising need for changes to their IT infrastructure. This need is becoming even more urgent as they continue to migrate operations to the cloud. Leveraging modern cloud applications and resources within an existing legacy agency environment requires IT agility to maintain the balance of security while keeping pace with an agency’s mission.
How to choose your SAP automation foundation to enable hyperautomation success
Automatically Update URL Blocklists in Zscaler Using Torq
Blocking access to certain URLs is a simple, effective strategy for protecting users and the network. But, in a world where new and increasingly sophisticated scams seem to appear almost weekly, the task of maintaining that list can become overly burdensome when performed manually. Torq offers a number of ways to automate URL blocklist management, reducing manual effort and speeding up response to new threats.
How Automation and AI are Transforming Service Desks in 2022?
To modernize how organizations do business worldwide, they are adopting AI along with digital technologies. By doing so, companies strive to enhance productivity and efficiency and innovate new customer and employee experiences that will improve competitiveness. Organizations and their leaders must adopt a transformational and holistic mindset to succeed. They need a digital transformation that solves customer experience for multiple service queries.
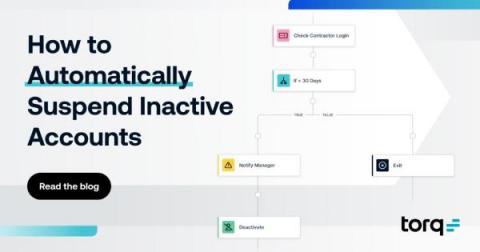
How to Automatically Suspend Inactive Accounts Using Torq
Contractors, freelancers, and other temporary workers have become essential parts of the modern enterprise. For IT and security teams, these individuals present unique challenges compared to full-time workers—and potential risks. The ‘offboarding’ process for these contractors is often less formal than bringing them on. Meaning, many just stop using their entitlements and accounts without actually closing them. These dormant accounts can pose serious risks to the organization.
Puppet and Government: Maintaining compliance in complex hybrid cloud environments
This blog is the third in a four-part series about how Puppet can help government agencies meet compliance and security requirements. Read the second post here. Government agency IT departments know that migrating applications to the cloud can improve efficiency, increase visibility, and reduce costs. They also recognize the value in keeping some operation resources on-premises.
Change in behavior: multiple cf-execd processes
Recently we introduced new feature where you can trigger agent runs and report collection from the Mission Portal UI. This required our daemon cf-execd to behave a bit differently when periodic agent runs occur. Previously the daemon would create a new thread in which to run cf-agent, capture output, wait for completion and move on. We changed the behavior so that the daemon forks itself and then fork/execs cf-agent as before, with the forked cf-execd processing agent run output.