Operations | Monitoring | ITSM | DevOps | Cloud
Automation
5 Tips for Helping Your Workforce Adapt to Automation
There has been a rapid incline in the use of automation in many day-to-day activities, making life a bit simpler. Whether it’s through the implementation of chatbots or automated reporting tools, automation has become a new norm. It’s meant to make workloads a lot easier, as well as improve efficiency. However, not everyone may see it that way. The simple notion of automation taking over your job can cause a lot of stress, anger, and/or anxiety.
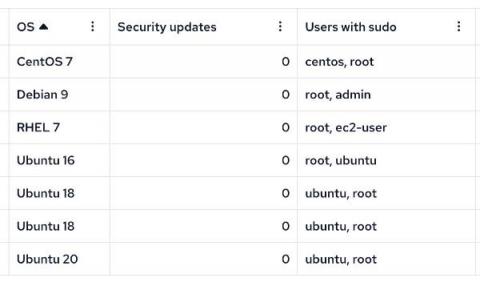
Secure your hosts with CFEngine Build modules
Last year, we launched functionality for users to add policy for reporting data, compliance reports, promise types, and other code as modules. With CFEngine Build, users can manage and update their own policy, the default policy and any additional modules separately. This makes it very easy to utilize policy or other modules written by the CFEngine team, or other community members. In this post we will take a look at using some modules to improve the security of our infrastructure.
SecOps in a Post-Covid World: 3 Security Trends to Watch
By now, you’ve probably read loads of articles that discuss the COVID-19 pandemic’s impact on business, politics, the economy and much more.But what about SecOps? What permanent effects has COVID wrought on the way businesses secure IT assets? Let’s explore those questions by examining three key security trends that promise to endure long after the pandemic has finally receded.
CentOS 8 is end-of-life: Now what?
There were many reasons people came to use CentOS as an alternative Linux platform to Red Hat Enterprise Linux (RHEL). CentOS was originally built as a downstream release of RHEL, which was free to use without support. CentOS became the de facto standard for many organizations that did not want to use RHEL for production workload, since it’s basically the same thing, just rebranded.
Collecting Support data with the Puppet Enterprise Support Script Part 1
Collecting Support data with the Puppet Enterprise Support Script Part 2
CSPM - Intro to Torq Webinar
Building the future of DevOps automation
Today, we’re starting Relay by Puppet, a new initiative to build the future of cloud-based DevOps automation. This post captures our musings about the evolving world of cloud-native infrastructure and how Relay addresses this evolution.
4 ways automation can improve your security posture
Security is top of mind for many organizations—and for good reason. Recovering from a data breach is extremely costly. In fact, the average data breach costs more than $8.6 million in the US. One of the best ways to defend against cyberthreats is by adopting and implementing security automation.