Operations | Monitoring | ITSM | DevOps | Cloud
%term
12 Days of Christmas Updates | Day Four: Auto-provisioning support for SAML SSO
Day 4 Update is auto-provisioning support for SAML SSO! Now SAML SSO users can log into Raygun without manual setup.
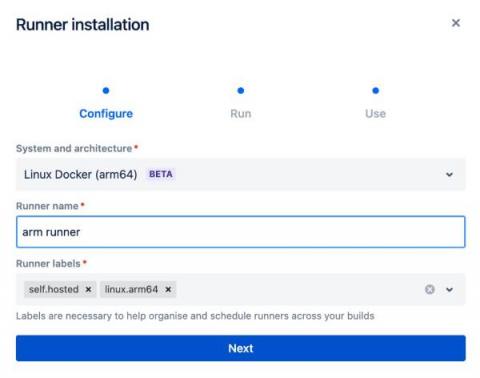
Third-party secrets are now supported in Bitbucket Pipelines
Bitbucket Pipelines is excited to announce support for CI/CD third-party secrets – a powerful new feature that enables you to seamlessly retrieve secrets directly from your preferred secret store. This enhancement ensures your workflows remain efficient and secure. Now, you can set up your own integration and customize the utilization of your secrets to suit your needs.
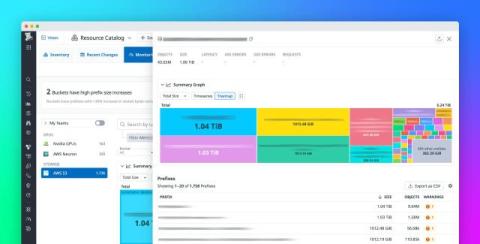
Optimize and troubleshoot cloud storage at scale with Storage Monitoring
Organizations today rely on cloud object storage to power diverse workloads, from data analytics and machine learning pipelines to content delivery platforms. But as data volumes explode and storage patterns become more complex, teams often struggle to understand and proactively optimize their storage utilization. When issues arise—such as unexpected costs or performance bottlenecks—these teams frequently lack the visibility needed to quickly identify and resolve root causes.
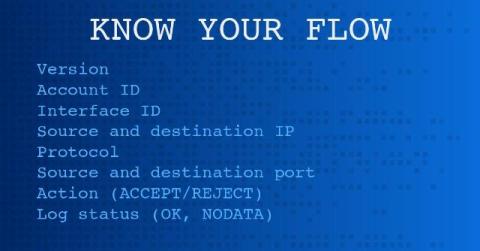
Understanding the Differences Between Flow Logs on AWS and Azure
AWS VPC flow Logs and Azure NSG flow Logs offer network traffic visibility with different scopes and formats, but both are essential for multi-cloud network management and security. Unified network observability solutions analyze both in one place to provide comprehensive insights across clouds.
What Do Most Corporations Do With Returned Computers?
When computers are returned to a corporation, they don’t simply disappear into storage or landfills. Companies often implement structured processes to make the most of these devices while adhering to regulatory and ethical standards. Managing returned computers is a practical and pressing concern for corporations, whether dealing with employee's offboarding, end-of-life hardware, or upgrades. The process involves multiple considerations, from data security to environmental compliance.
How to Mitigate DDoS Attacks and the Impact on Availability
Distributed Denial of Service (DDoS) attacks are intended to overwhelm a network or server and cause failure or work stoppage. DDoS attacks first appeared in the mid-1990s and continue to the present day. Far from going away, they have become more prevalent: in the first quarter of 2024, the number of DDoS attacks against web servers increased by 93% compared to the same period a year earlier. One survey found that nearly 70% of organizations experienced 20 to 50 DDoS attacks per month.
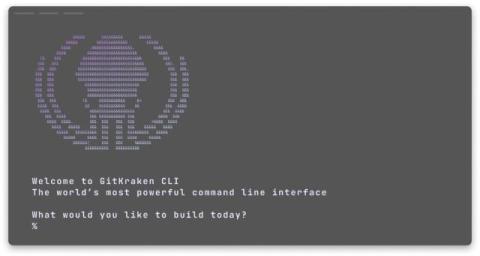
Git + Microservices: Mastering Multi-Repo Complexity with GitKraken's New CLI Tool
We’ve all been there: working a feature that spans multiple Git repositories, doing your best to coordinate pull requests and save the reviewers from “review-hell” as they try to piece together how everything fits across the repositories… When a change impacts more than one microservice, the coordination can become a mess of disconnected PRs spanning many repos, each dependent on the other to avoid breaking something critical.
What is Configuration Management? IT Beginners Guide
Configuration Management is the backbone of IT Service Management, providing a clear and reliable map of your IT landscape. It ensures that assets required to deliver services are controlled and that accurate information about them is available when needed. In ITIL 4, it's a crucial part of the Service Management Practice section within the Service Value System.
Cloud-Based Monitoring & Automation | Webinar by NiCE and Kelverion
Join us for an exclusive webinar presented by NiCE and Kelverion, where we’ll dive into how to enhance your IT infrastructure through cloud-based monitoring and automation. This session will focus on leveraging the power of Microsoft Azure and System Center Operations Manager Managed Instance (SCOM MI) for seamless integration, real-time monitoring, and automated workflows.