Build a CircleCI Dashboard to visualize all your CI/CD data
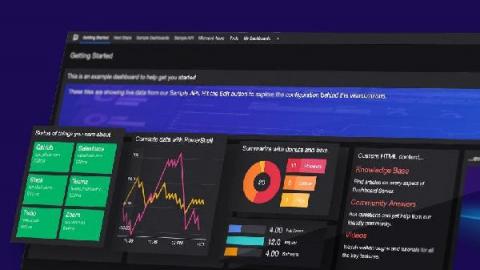
If you’ve checked out SquaredUp for SCOM/Azure and decided for one reason or another that it wasn’t the right tool for you, you are in for a treat! Our latest free tool, Dashboard Server, addresses many of the same pain points, but this time, for a variety of platforms not tied to SCOM or Azure. On the flip side, if you’re currently using SquaredUp for SCOM/Azure, don’t click away!