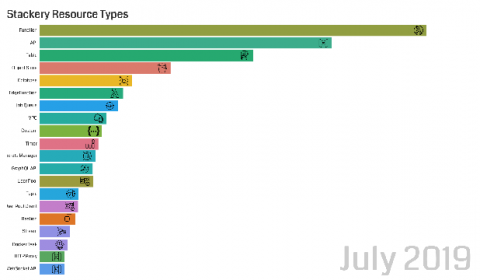
Why an OS Monitoring tool is not sufficient for Monitoring VMware and Other Virtualization Technologies
You have management software that you’ve used for your Linux or Windows servers. Can’t you just deploy a Linux agent and monitor a VMware vSphere/ESX server, or a Windows agent to monitor a Microsoft Hyper-V server? This is a very common question that comes up in any discussion on VMware monitoring and virtualization management. After all, when a VMware ESX server boots, the administrator gets to a Linux login prompt and can login to a Linux operating system.