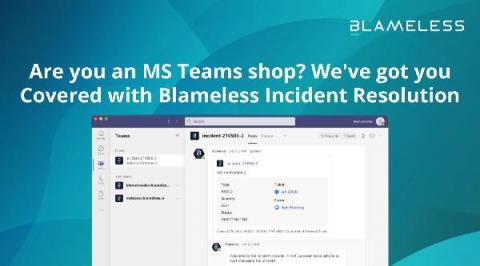
Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
EMR workload continuity with Elastigroup
Amazon’s Elastic Map Reduce or EMR, makes it easy to set up, operate and scale big data environments. This enables data scientists and developers to rapidly analyze massive amounts of structured and unstructured data. Combined with Spot by NetApp’s Elastigroup, data scientists can reliably run EMR core and task nodes on highly affordable EC2 spot instances.
Monitor key metrics and visitor demographics in NGINX with the new Grafana Cloud integration
We are happy to announce that the NGINX integration is available for Grafana Cloud, our composable observability platform bringing together metrics, logs, and traces with Grafana.
How Lowe's meets customer demand with Google SRE practices
At Lowe’s, we’ve made significant progress in our multiyear technology transformation. To modernize our systems and build new capabilities for our customers and associates, we leverage Google’s SRE framework and Google Cloud, which helps us meet their needs faster and more effectively. With these efforts, we’ve been able to go from one release every two weeks to 20+ releases daily—about 20X more releases per month.
You Can Now Use observIQ Completely Free
Today, we’re excited to announce a new completely free pricing tier for observIQ: the 3-day free plan. With the observIQ free plan, you can ingest and index up to 3 gigabytes of logs per day with a 3 day rolling retention period.
Breaking Things on Purpose
Get started with Gremlin's Chaos Engineering tools to safely, securely, and simply inject failure into your systems to find weaknesses before they cause customer-facing issues. Updated June 7, 2021.
Classic Event Viewer Retires
Quick Demo: A Day in the Life of a Remote Knowledge Worker
Do you make it a habit of connecting to the free Wi-Fi network at the coffee shop, restaurant, hotel, airport or even in-flight on the airplane to save on your cellular data minutes? Watch this short 2-minute video to see what happens if you connect to a wireless network with a malicious cyber threat actor performing Man-in-The-Middle (MiTM) attacks to unsuspecting victims.
AIOps 101
In all internal and external conversations that I’ve had in the recent weeks, almost always the discussion veers towards AIOps. This blog summarizes research that I’ve done into understanding AIOps – what it is, why analysts and customers are so interested in this technology and what are some of the benefits that it offers.
Protecting Windows protected processes
This quick blog is the first in a two-part series discussing a userland Windows exploit initially disclosed by James Forshaw and Alex Ionescu. The exploit enables attackers to perform highly privileged actions that typically require a kernel driver.