Recommended Server Room Temperature and Humidity
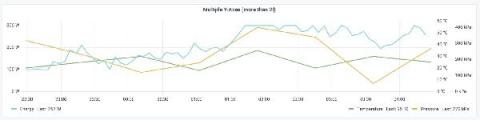
What are the ideal server room temperature and humidity levels where you store your servers? This is an important question you should know the answer to whether you are responsible for managing racks of servers or a small business owner with a single server. Servers house your data, files, and other information to make it easily accessible from any connected workstation. If the server room gets too hot or too humid, it can cause your servers to overheat and fail.