Key Takeaways from DEJ's IT Performance Management Study
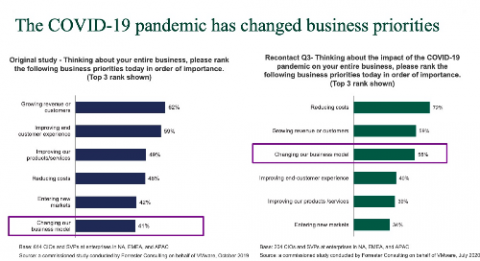
It goes without saying that 2020 has been a challenging year for businesses. Faced with unexpected and unfamiliar hurdles, organizations have been under immense pressure to maintain or improve performance in all areas of their business. But this has also been a year of innovation. We’ve seen modern organizations embrace new, innovative technologies and tactics that have reshaped the way they manage IT performance.