5 Strategies for Decreasing API Latency and Improving App Performance
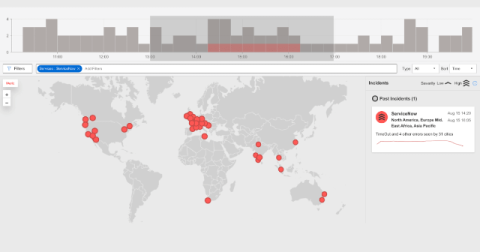
Application performance can make the difference between retaining or losing customers, with delays beyond a few seconds leading to dropped conversions. Performance testing and monitoring are vital for improving the overall user experience, achieving a competitive advantage, enhancing resource efficiency, enabling scalability, and reducing costs.