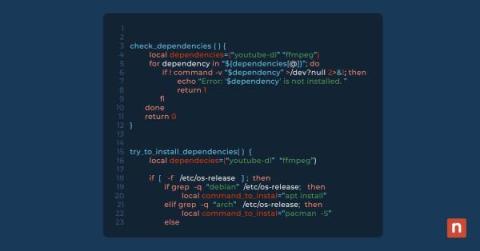
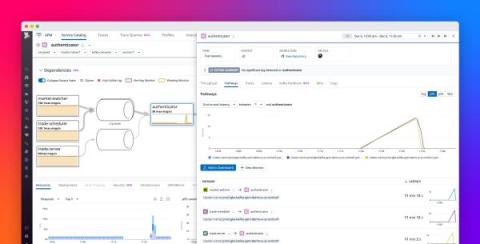
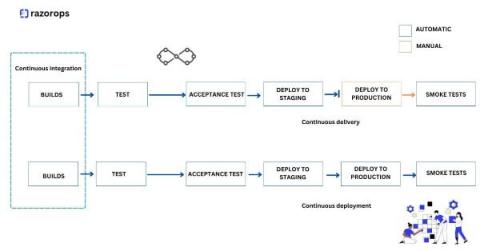
How Much Does Endpoint Management Software Cost?
Organizations today have seen a significant increase in endpoints due to the rapid growth of remote and hybrid work, along with the emerging trend for employees to bring their own devices to work. With all these additional endpoints to keep track of and manage, it has become all the more necessary for IT managers and cybersecurity professionals to implement or upgrade their endpoint management software to ensure that all devices are secure and up to date.