Custom Resources with HAProxy Kubernetes Ingress Controller
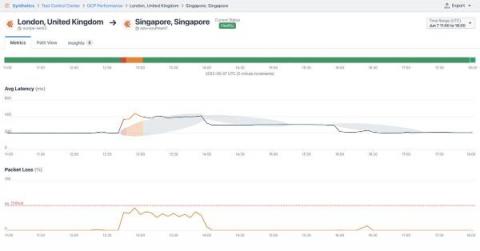
HAProxy Kubernetes Ingress Controller provides custom resources named Backend, Defaults, and Global that let you manage ingress controller settings more efficiently. To start using them right away, check the documentation for steps and examples. In this blog post, you’ll learn why custom resources are such a powerful feature and see tips for getting the most out of them.