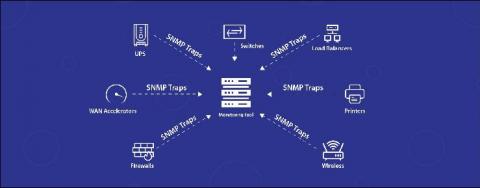
Quick start monitoring by using lightweight monitors
There are instructions to get started with IPHost Network Monitor, covering most typical situations. However, using the defaults (for both monitors parameters and for network discovery) when looking for hosts and/or monitors can result in rather slow setup. In most cases, it is simpler to create "draft", lightweight monitors just to make sure the service exists and accepts connections, and add actual protocol-specific checks as required.