How 1Password Relies on Checkly for Secure System Health Monitoring for Thousands of Business Customers
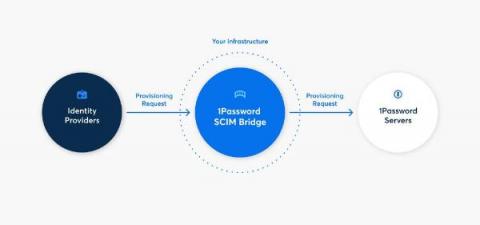
1Password uses Checkly to provide transparent, advanced synthetic monitoring to 1Password SCIM bridge customers 1Password is a leader in human-centric security and privacy, with a solution that’s built from the ground up to enable anyone—no matter the level of technical proficiency—to navigate the digital world without fear or friction when logging in.