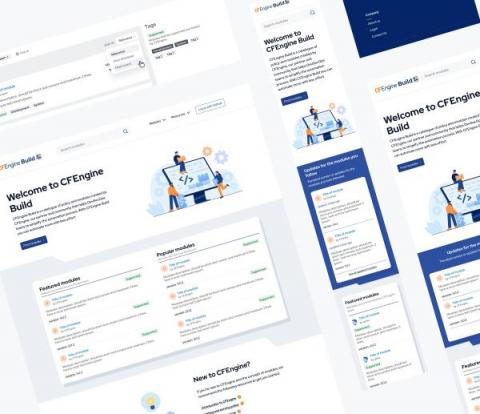
How we designed CFEngine Build, a complete journey
Have you ever wondered how a site was designed and how the ideas were conceptualized into a webpage? If your answer is yes, you are in the right place! In this post, I will show you our journey to create our latest web page, CFEngine Build. From start to finish, how did we do the design and make the design decisions? So without further delay, let’s jump straight in!