Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
You've Achieved GDPR Compliance-Now What?
General Data Protection Regulation (GDPR). Most of us remember the months and weeks leading up to the deadline. We did whatever needed to be done to achieve compliance. Now it seems like a distant memory. And the pressure is mostly off. But in other ways, it was just the beginning. As you continue creating your day-to-day compliance strategy, you might find that the tactics that got you to the finish line were more short-term solutions that won’t necessarily stand long-term.
Interview with Cybersecurity Specialist Babak Pasdar, CTO of Acreto
For our latest expert interview on our blog, we’ve welcomed Babak Pasdar to share his thoughts on the topic of cybersecurity and his journey as the CTO of Acreto. Babak Pasdar is a globally recognized innovator, cybersecurity expert, author, and entrepreneur best known for his multiple innovations in the area of cloud security.
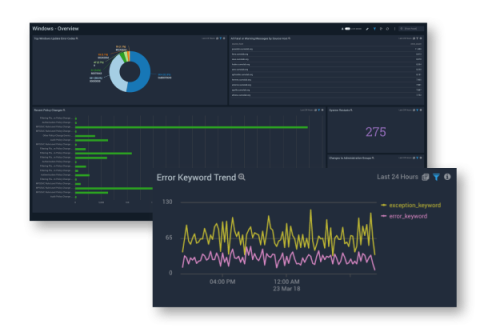
How to streamline Windows monitoring for better security
History of Open Source Identity Management (part 2)
This is the second blog post (part 1 available here) where we look at the history of open source identity management. This post focuses on Oauth and OpenID, the protocols currently used in modern applications and services. This post does not cover the technical details of the open source identity management standards, which are explained very well in this Okta blog post. Rather, it explains the origins of Oauth and OpenID, and provides insights on the context that led to their creation.
Run your Ubuntu in US Government Clouds
In August 2016, the United States government announced a new federal source-code policy, which mandates that at least 20% of custom source code developed by or for any agency of the federal government must be released as open-source software (OSS). The memo of this policy also states that the Federal Government spends more than $6 billion each year on software through more than 42,000 transactions. Obviously, this is a huge business for all open-source developers.
Kubernetes Security: 9 Best Practices for Keeping It Safe
Kubernetes dominates the container orchestration market in every way. According to the latest State of Kubernetes and Container Security study, 88% of enterprises utilise Kubernetes to manage a portion of their container workloads. Kubernetes and other orchestration systems have given software deployment and management a new level of robustness and customization. They also brought attention to the current security landscape's shortcomings.
Better Protect your Corporate Data While Ensuring Optimal Service Delivery for your Business Lines
Within an organization, the Network Operations Center (NOC) and Security Operations Center (SOC) teams need to work together to maintain optimal network performance in addition to ensuring both overall security and the availability of IT services for business lines. In the past, these two teams were focused on two separate objectives, using different tools to do so and often running specific processes.
Mail Assure achieves top result in Virus Bulletin testing
We’re pleased to announce that N-able™ Mail Assure has received a top result in an independent test conducted by the Virus Bulletin, an industry-renowned test laboratory and an important reference for specialists and businesses concerned with computer security. So, what exactly is this test and how did Mail Assure achieve such a great score?
Obfuscate user data with Session Replay default privacy settings
Session Replay enables you to replay in a video-like format how users interact with your website to help you understand behavioral patterns and save time troubleshooting. Visibility into user sessions, however, can risk exposing sensitive data and raise privacy concerns. For example, a user session may include typing in a credit card or social security number into an input field.