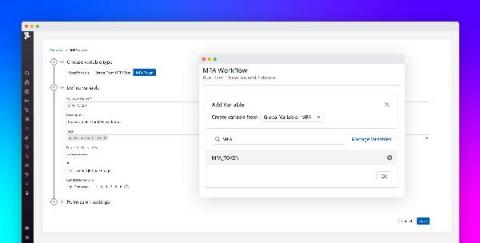
Introducing multi-factor authentication in Datadog Synthetic tests
Multi-factor authentication (MFA) is an increasingly popular method for securing user accounts that requires users to provide two or more pieces of identifying information when logging into an application. This information can consist of unique verification links or codes sent to the user’s phone or email address, as well as time-based one-time passwords (TOTPs) generated by authenticator applications or hardware.