How Orange Business Services is building a better SIEM with Elastic
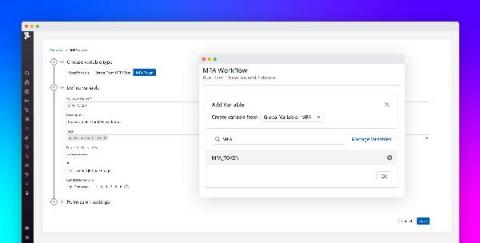
I’m a security analyst at Orange Business Services in Paris, and one of my current projects for the Orange Group is implementing a new SIEM based on the Elastic Stack. In this blog post, I’ll share why we chose Elastic and how we were able to integrate Elastic into our existing SIEM, resulting in faster investigations and saving our engineers’ time. So follow along.