Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
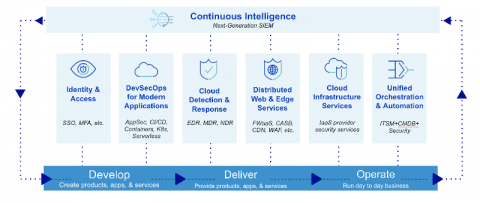
A New Framework for Modern Security
Know your access control: RBAC vs. ABAC
Working together successfully as a team — especially in this increasingly remote world — is all about collaboration. As part of that collaboration, it’s critical that team members have access to the files and programs they need to accomplish their jobs, and that access should be easily revocable for when employees change roles or leave the company. This is achieved through access control, which, simply put, defines who is allowed to access what.
How to Monitor, Manage, and Secure Active Directory
Data Security for Big Data
Big data security is a term used for all collective measures taken to protect both data and analytical processes from theft, attacks or all other malicious activities. Just like other forms of cybersecurity, big data security is about attacks originating from every online or offline sphere. Companies operating on the cloud face multiple challenges including online information theft, DDoS attacks and ransomware.
Gaining holistic visibility with Elastic Security
Let’s talk visibility for a moment. Security visibility is a data-at-scale problem. Searching, analyzing, and processing across all your relevant data at speed is critical to the success of your team’s ability to stop threats at scale. Elastic Security can help you drive holistic visibility for your security team, and operationalize that visibility to solve SIEM use cases, strengthen your threat hunting practice with machine learning and automated detection, and more.
Detecting & Preventing Ransomware Through Log Management
As companies responded to the COVID-19 pandemic with remote work, cybercriminals increased their social engineering and ransomware attack methodologies. Ransomware, malicious code that automatically downloads to a user’s device and locks it from further use, has been rampant since the beginning of March 2020. According to a 2020 report by Bitdefender, ransomware attacks increased by seven times when compared year-over-year to 2019.
Detect Ransomware in Your Data with the Machine Learning Cloud Service
While working with customers over the years, I've noticed a pattern with questions they have around operationalizing machine learning: “How can I use Machine Learning (ML) for threat detection with my data?”, “What are the best practices around model re-training and updates?”, and “Am I going to need to hire a data scientist to support this workflow in my security operations center (SOC)?” Well, we are excited to announce that the SplunkWorks team launched a new add-
Kubernetes Security
FabFit - Not So Fun for Customers with Stolen Payment Data
Our sources state that there has been a 20% increase in web-skimming attacks since the outbreak of the COVID-19 virus. Recently, we have witnessed some high-profile Magecart attacks. The latest Magecart attacks include; American Payroll Association, music giant – Warner Music Group, and lifestyle subscription brand – FabFitFun.