Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Best practices for monitoring authentication logs
If you are running a user-facing web application, you likely implement some form of authentication flow to allow users to log in securely. You may even use multiple systems and methods for different purposes or separate groups of users. For example, employees might use OAuth-based authentication managed by a company-provided Google account to log in to internal services while customers can use a username and password system or their own Google credentials.
Detect CVE-2020-8554 using Falco
CVE-2020-8554 is a vulnerability that particularly affects multi-tenant Kubernetes clusters. If a potential attacker can create or edit services and pods, then they may be able to intercept traffic from other pods or nodes in the cluster. An attacker that is able to create a ClusterIP service and set the spec.externalIPs field can intercept traffic to that IP. In addition, an attacker that can patch the status of a LoadBalancer service can set the status.loadBalancer.ingress.ip to similar effect.
What's new in Sysdig - December 2020
Welcome to another monthly update on what’s new from Sysdig. Our team continues to work hard to bring great new features to all of our customers, automatically and for free!
New Vulnerability Exposes Kubernetes to Man-in-the-Middle Attacks: How to Mitigate CVE-2020-8554
A few weeks ago a solution engineer discovered a critical flaw in Kubernetes architecture and design, and announced that a “security issue was discovered with Kubernetes affecting multi-tenant clusters. If a potential attacker can already create or edit services and pods, then they may be able to intercept traffic from other pods (or nodes) in the cluster.” If a hostile user can create a ClusterIP service and set the spec.externalIP field, they can intercept traffic to that IP.
In the aftermath of the SolarWinds hack, IT Ops leaders should reconsider on-premises tooling investments
Solarwinds is a 21-year old publicly traded monitoring and network management vendor with 300,000+ customers across the world. It’s familiar to IT operations and monitoring teams across enterprises big and small. And this week, it found itself in the news for all the wrong reasons.
Will XDR Change Incident Response?
Extended Detection and Response (XDR) is a new security technology that promises to change the way security organizations operate, and introduce important efficiencies to day-to-day processes. In particular, XDR is expected to have a huge impact on incident response teams. In this article, we’ll explain the basics of XDR, show how it addresses incident response challenges, and how it can transform traditional processes in the SOC.
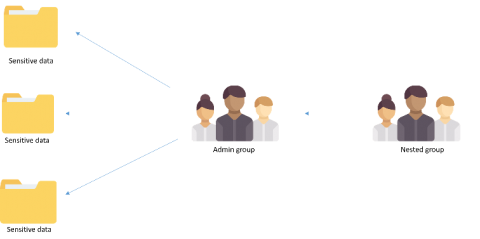
IT security under attack: Why are group memberships so crucial?
Security groups either make or break your IT security. Group memberships are responsible for administrative access in your your network and define access to other privileged resources and data on your domain. Ever wondered how a simple misconfiguration of a group membership could lead to a security incident? This blog elaborates the most common misconfiguration or security loopholes that can cause damage to the sensitive data in your network.
Combining supervised and unsupervised machine learning for DGA detection
It is with great excitement that we announce our first-ever supervised ML and security integration! Today, we are releasing a supervised ML solution package to detect domain generation algorithm (DGA) activity in your network data. In addition to a fully trained detection model, our release contains ingest pipeline configurations, anomaly detection jobs, and detection rules that will make your journey from setup to DGA detection smooth and easy.