Steps to Taming Hybrid Cloud Complexity: Eliminating Visibility Gaps & Enabling Actionable AI-Powered Insights
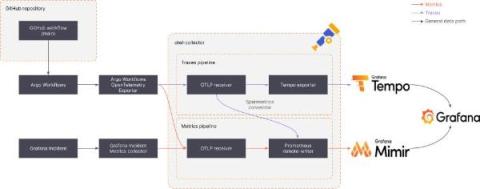
For years “the move to the cloud” implied a singular event – a singular migration to a singular entity. It all sounded so simple. Yet, the “simple” act of moving to the cloud stands in stark contrast to the reality of today’s complex, hybrid IT estates where the overwhelming volume of data flows can make it challenging for IT teams to effectively pinpoint and rectify service incidents.