Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
AT Internet - Elevating Product Quality with Catchpoint
AT Internet, a digital analytics pioneer, helps companies measure and optimize the digital performance of their customers across all marketing channels. From data collection to in-depth analysis and the sharing of insights, AT Internet’s Analytics Suite Delta provides high-quality, GDPR-compliant data that optimizes decision-making company-wide.
Accelerating Root Cause Analysis of IT Incidents
The moment after an incident is resolved is perhaps the most relaxing for any IT team. When your system is finally functioning properly it puts the entire organization at ease, but the most daunting task is yet to come: root cause analysis (RCA). Akin to football teams watching previous plays to pinpoint areas of improvement, root cause analysis goes through data and finds what initially caused the incident.
Detecting CVE-2020-1472 (CISA ED 20-04) Using Splunk Attack Range
The recent disclosure of CVE-2020-1472 vulnerability by Microsoft showcases the need for tools that allow defenders to quickly replicate published exploit code, register attack data, and create signatures or other mitigations against released exploits with a high likelihood of exploitation against popular infrastructure or operating systems.
Partner Profile: NextBit Technologies
In some industries, Covid-19 has served as a war cry to push the lever on progressive digital initiatives. Urgency amid dire uncertainty created a reason to move forward and faster. Surveys have also indicated a much stronger focus on public cloud infrastructure, as IT leaders gravitate toward cost-effective, on-demand scalability.
Vendors Rejoice! Analyse your Bandwidth Usage
As a vendor, understanding your bandwidth usage is an invaluable insight into how packages are distributed across your user base and how specific users have grown over a timeframe.
VMware Tanzu Mission Control Expands Its Policy Management Capabilities
We are excited to announce the general availability of security policies and policy insights in Tanzu Mission Control. With the launch of these new capabilities, administrators can easily streamline and manage the security of their Kubernetes cluster fleet. They can also take advantage of the rich policy insights dashboard, which provides a centralized and holistic view of the current state of all policy events in their system.
How to ensure a seamless end-user experience: The ITOM Podcast [Episode 6]
The ITOM Podcast is back with an all new episode aimed to alleviate all your remote work woes in your IT environment. In the last episode, we discussed in detail about the need for compliance checks, major causes of compliance violations across industries, and the solution to help maintain network compliance. This week, we’ll dive into the end-user experience in this era of remote work.
We've grown up a little, got a bit smarter & we're looking sharp!
We’re well over a year old now, the team has doubled in size and things are going just swell here at Team_Cookdown. Since we launched, we’ve expanded our product range to include some awesome new solutions like Alert Sync and Discovery and added loads of new features to our existing SCOM toolkit; to bring you expertly crafted integrations solutions for two of the most established platforms in IT enterprise, SCOM and ServiceNow.
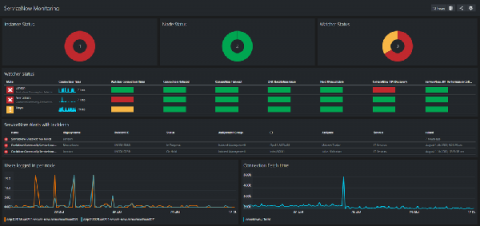
Unlock your ServiceNow Monitoring with Dashboards
Good news! We’ve created an awesome SquaredUp dashboard pack for our ServiceNow Monitoring MP! You can now enjoy our ServiceNow Monitoring MP and Dashboard pack for free, just click on the links below.