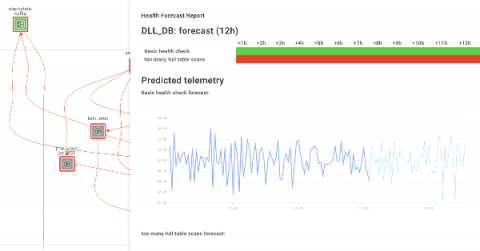
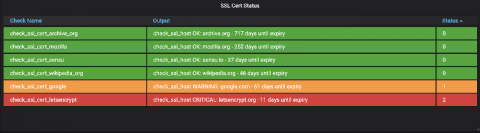
StackState's Health Forecasting
Forecasting health is vital in today's society. Who has the highest risk of getting a virus? Are you able to predict when this will happen? Knowing answers to these questions could save many lives. Forecasting the health of IT infrastructures is equally essential. Think of identifying databases that are about to stop serving requests in a timely matter, hard drives that are about to run out of space, or Service-level agreements (SLA's) that are about to cross the set thresholds.