A Comprehensive Guide to Migrating from Python 2 (Legacy Python) to Python 3
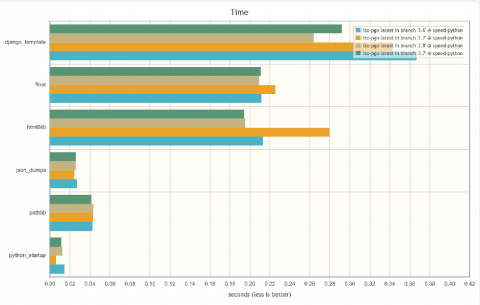
Python powers many applications we use in our day-to-day like Reddit, Instagram, Dropbox, and Spotify. The adoption of Python 3 has been a subject of debate in the Python community. While Python 3 has been out for more than a decade now, there wasn’t much incentive to migrate from the stable Python 2.7 in the earlier releases. If you’re still running on legacy python, it’s high time to migrate as it has reached the end of its life since Jan 2020.