Sumo Logic Partners with IP Intelligence Leader Neustar to Meet Growing Customer Needs at Scale
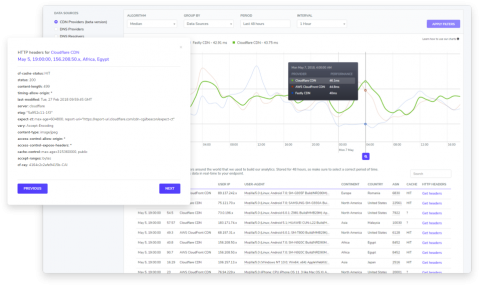
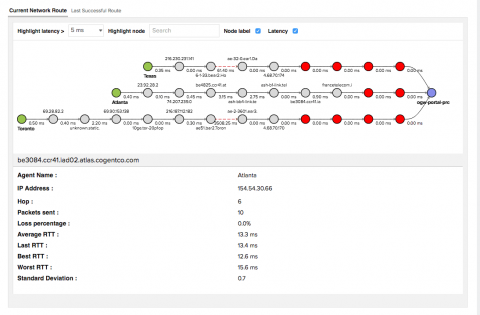
Customers are visiting your website, employees are logging into your systems and countless machines are talking to each other in an effort to deliver the perfect user experience. We’d like to believe that all of these individuals and machines are operating with the best of intentions, but how can we be so sure? One possible answer lies in the connecting device’s IP address and its respective physical location.