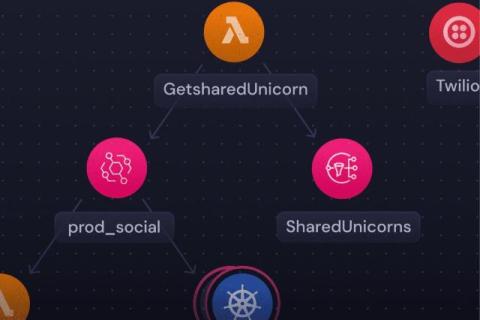
How to detect broken links with Playwright
One of our Slack community members recently asked if they could use Playwright and Checkly to detect broken links on their sites. They certainly can, and the answer to this question covers so many different Playwright concepts that it makes a perfect case for sharing Playwright features with the community. Let's unveil some links going nowhere! If you prefer the video version of this tutorial,