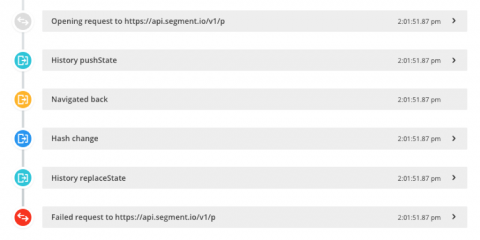
How to replicate user errors without the user with Breadcrumbs and Sessions
If you need to replicate a user error, you’ll know how difficult it can be to pinpoint the cause. Usually, you’d look at the stack trace or ask the user themselves. However, that’s a lot of guesswork, especially if the stack trace is obfuscated. We’ll show you how to replicate the error faster using Crash Reporting’s Breadcrumbs and the Real User Monitoring Sessions feature.