Making the Switch to Hosted Monitoring
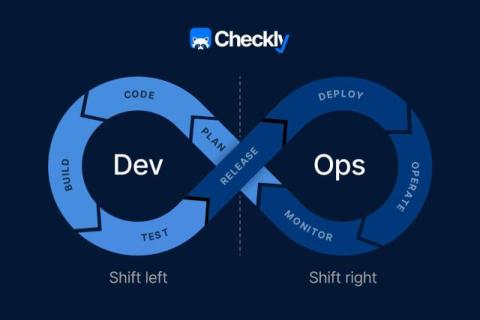
Implementing a monitoring solution is no small task; with your company's data growing, it can feel impossible. Often, small teams develop their own monitoring infrastructure because it is more cost-effective than a platform. But when your business grows, your data does, too. Monitoring can quickly become a bigger challenge than a small team can handle, and some companies need more resources to hire a developer dedicated to their monitoring.