How to detect and remove rootkit
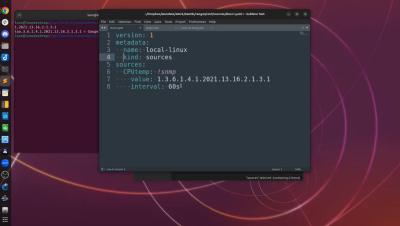
Rootkits are always hidden behind another program or file and as a result, detecting their presence is difficult. There are, nevertheless, several ways to detect rootkits in different operating systems and remove them. Watch the complete video to learn more.