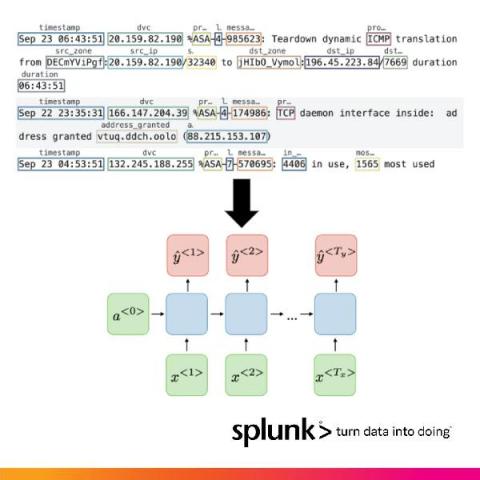
How Splunk Is Parsing Machine Logs With Machine Learning On NVIDIA's Triton and Morpheus
Large amounts of data no longer reside within siloed applications. A global workforce, combined with the growing need for data, is driving an increasingly distributed and complex attack surface that needs to be protected. Sophisticated cyberattacks can easily hide inside this data-centric world, making traditional perimeter-only security models obsolete.