Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
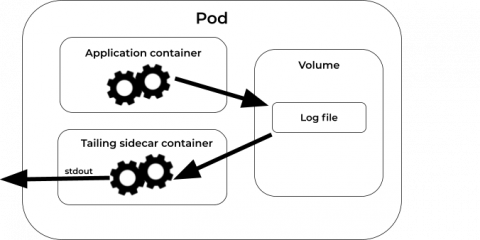
Tail your logs with Tailing Sidecar Operator
Elastic and Confluent partner to deliver an enhanced Kafka + Elasticsearch experience
Today, we are pleased to announce a partnership with Confluent to jointly develop and deliver an enhanced product experience to the Kafka-Elasticsearch community. Kafka is — and has been since the very early days — an important component of the Elastic ecosystem.
Improve Monitoring and Observability With The Catchpoint and Sumo Logic Integration
Sumo Logic is a cloud-based log management and analytics service that leverages machine-generated big data to deliver real-time IT insights. We’re excited to share that you can now easily integrate Catchpoint and Sumo Logic, giving you a number of fantastic benefits. The integration involves pushing data from Catchpoint to Sumo Logic using Webhooks and then query the data to build visualizations. Why do we use Webhooks?
Logz.io Debuts Multiple Tracing Accounts and Jaeger Architecture Visualization
Logz.io has pressed hard to align our tracing and metrics analytics capabilities over the past year. And as our technology advances, so does our service. We are announcing Multiple Tracing Accounts with Logz.io Distributed Tracing, aligning it with our logging and metrics tools. Complementing multiple data sources for metrics and logs, Logz users can segment their data according to sources and teams for better organization.
Advanced Link Analysis: Part 2 - Implementing Link Analysis
Link analysis, which is a data analysis approach used to discover relationships and connections between data elements and entities, has many use cases including cybersecurity, fraud analytics, crime investigations, and finance. In my last post, "Advanced Link Analysis: Part 1 - Solving the Challenge of Information Density," I covered how advanced link analysis can be used to solve the challenge of information density.
Threat Hunting with Threat Intelligence
With more people working from home, the threat landscape continues to change. Things change daily, and cybersecurity staff needs to change with them to protect information. Threat hunting techniques for an evolving landscape need to tie risk together with log data. Within your environment, there are a few things that you can do to prepare for effective threat hunting. Although none of these is a silver bullet, they can get you better prepared to investigate an alert.
Best Practices For Logging In AWS Lambda
Today, we’ll cover some of the ways you might find quite useful in your everyday work. We’ll go through some of the logging best practices in AWS Lambda, and we will explain how and why these ways will simplify your AWS Lambda logging. For more information about similar topics, be sure to visit our blog. Let’s start with the basics (and if you have the basics covered, feel free to skip ahead): How does logging work with AWS Lambda?
How to Monitor RabbitMQ Performance: Tools & Metrics You Should Know About
Nowadays, most applications we build are composed of microservices and distributed in nature. In such a setup, communication between these microservices is crucial, but can, unfortunately, cause some headaches. The first thing I check when I’m troubleshooting a bug in production is inter-service communication. Having a reliable tool at your disposal to take care of this can reduce a lot of stress. RabbitMQ, a hybrid messaging broker, is one such tool.