Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
What's new in Kubernetes 1.18?
Kubernetes 1.18 is about to be released! After the small release that was 1.17, 1.18 comes strong and packed with novelties. Where do we begin? There are new features, like the OIDC discovery for the API server and the increased support for Windows nodes, that will have a big impact on the community. We are also happy to see how some features that have been on Alpha state for too long are now being reconsidered and prepared for the spotlight, like Ingress or the API Server Network Proxy.
Kublr 1.17 adds config page on UI, supports latest Kubernetes release (one of only a few providers)
If you’re an advanced Kubernetes user, you’ll likely want to configure parameters for specific use cases. While with Kublr, the most flexible Kubernetes platform on the market, literally everything is customizable (except, of course, if you want to replace Kubernetes with a different container orchestrator), a lot of the customization in the previous versions was still done via command line.
How I Built a Machine Learning Pipeline on AWS for Under $7 a Day
Andreessen Horowitz recently published a blog about the Heavy Cloud Costs and Scaling Challenges of The New Business of AI, in which they describe how AI companies are facing cloud cost challenges, which are impacting their margins. As someone who used to manage a fully home-grown on-site distributed speech recognition platform for an industry leader, I know firsthand that ML can be expensive and challenging to maintain. However, it doesn’t have to be.
Why I don't hate ITIL (aka ITIL in a DevOps World)
When I read Greg Ferro’s infamous “Why I hate ITIL so much” blog back in 2015, I have to admit that I agreed with many (albeit not all) of what he said. Maybe it’s the issues that I have with authority in general, or maybe it’s my many years of working within the constraints of ITIL and ITSM in operating systems and services – but I truly believed (and still do) that well-educated, experience and consensus-based pragmatism is what actually gets things done.
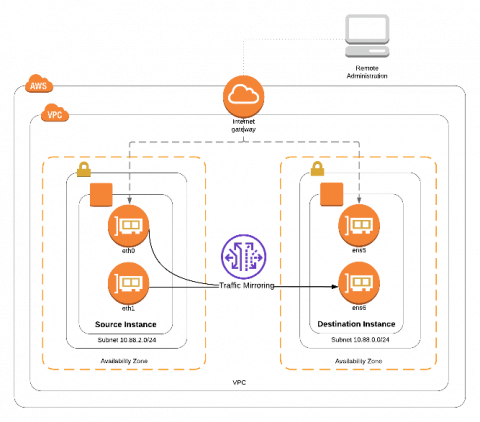
Amazon VPC Traffic Mirroring
Monitor vSphere with Datadog
VMware vSphere is a server virtualization platform that enables organizations to provision and manage virtual machines at scale. With its comprehensive suite of products, vSphere helps companies manage datacenter resources, migrate workloads without downtime, run applications with high availability, and more. To keep tabs on dynamic vSphere environments and effectively address resource bottlenecks, you need deep visibility across every part of your infrastructure.
Why we moved from Slack to Discord?
Today, at Qovery we have moved from Slack to Discord. We are a software company that is solving developer problems - application deployment. Solving developer problems required to have a close contact with the developers community. For team communication, we used a dedicated Slack workspace, for community communication - another one. Discord has been a real lifesaver for us. Let's start to tell you why..
Top Monitoring Tools for DevOps Engineers and SREs
Overcoming DNS barriers for Kubernetes Scaling
It was a cloudy winter morning when I had arrived at the office and found, to our horror, that a Kubernetes cluster was suffering from extremely high CPU and network usage and had become almost completely non-functional. To make things worse, restarting the nodes (the go-to DevOp solution), seemed to have absolutely no effect on the issue. Something was poisoning the network and we had to find out what it was and fast.