Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
3 mistakes I've made at the beginning of an incident (and how not to make them)
The first few minutes of an incident are often the hardest. Tension and adrenaline levels are high, and if you don’t have a well-documented incident management plan in place, mistakes are inevitable. It was actually the years I spent managing incidents without the right tools in those high-tension moments that inspired me to build FireHydrant. I built the tool I wished I’d had when I was trying to move fast at the start of incidents.
Development Velocity (And How To Balance Reliability)
Taking Your Kubernetes Helm Charts to the Next Level
Helm is a deployment tool for Kubernetes objects that supports package management, dependencies, and templating. In this article, we will explore how to optimize your Helm charts. To follow along, you’ll need a basic understanding of Helm and will have ideally written and deployed some basic Helm charts.
Shipa Product Updates - June 2022
Summer is finally here in the Northern Hemisphere and as we work on getting our collective outdoors time in, we also have been busy at work making some great enhancements to Shipa. We kicked off June with a great webinar with PeladoNerd focusing on LATAM. We continued to focus on building and enhancing Shipa.
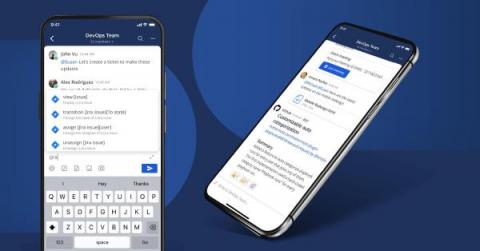
Join the Mattermost mobile beta program: v2.0 is now live!
Get ready for the future of Mattermost mobile. Beta testers can now access Mobile v2.0, including multi-server support — our most requested mobile feature ever. We’re also bringing you a number of usability enhancements and performance improvements to make you productive on the go. If you want to be on the cutting-edge of Mattermost mobile development, we’d encourage you to join the mobile beta program today.
Common DevOps Roles and Responsibilities
DevOps-oriented engineers live at the intersection of IT operations and software development: understanding much of what it takes to maintain IT infrastructure while also being able to write code and deploy new services. DevOps-minded teams not only create services — they also maintain them. A DevOps structure forces teams to take accountability for their applications and infrastructure instead of allowing developers to throw code over the proverbial wall to IT operations.
Announcing Qovery EC2: Deploy your apps on AWS for $20/m
Announcing Qovery V3: A brand new web interface
Prevent XSS attacks with browser testing
Security is a never-ending battle on the web. You can have a server up in just a few minutes, and the next minute, someone is already trying to hack into it. These attacks could be automated using malicious bots or launched manually. Websites can be targeted by a malicious user trying to compromise your web presence or data. Cross-site scripting (XSS) is just one type of attack your site may be vulnerable to.