Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
How the Eco Value Report gives your time back
Trunk-based vs. feature-based development
When you are the only dev building a software project, you can create and modify your code according to personal preference. When you contribute code to a team-run project, you need to follow a standardized set of guidelines and coordinate precisely with other team members. Standard guidelines and coordinated work effort are vital to the success of every team-based software development project.
The Path to Continuous Cloud Optimization
Implementing change in an organization always has its challenges, and for it to be successful it requires support from executive management. For one of our large Managed Service Provider (MSP) clients, their new CIO was focused on making their customer’s cloud consumption more efficient, with the outcome being cost savings.
Product Roundup: New Blameless Features in June 2022
Feature Highlight: Audit Logs
Audit Logs automatically record all user activities across all of your applications and team members. Audit Logs provide all the information you need to assess changes made to your account, such as IP address, date and time (displayed in your timezone), geo-location (accurate to the city), and the team members involved.
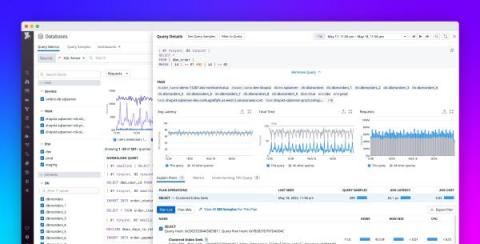
Monitor SQL Server and Azure managed databases with Datadog DBM
Datadog Database Monitoring (DBM) provides comprehensive visibility into SQL queries running on your databases. Using DBM, you can troubleshoot database performance issues by drilling into frequently used queries and analyzing historical trends in your queries’ metrics and execution plans. Whether you operate self-hosted SQL Server instances or leverage Azure’s fully managed services, DBM can provide deep visibility into the databases your application depends on.
Platform.sh announces $140m series D round of funding
Today is a big moment in the Platform.sh story and a bright day to celebrate in our seven-year history. This latest round of fundraising comes at the perfect time. We’ve already laid the groundwork by providing clients with the most efficient, most powerful management service to build and run web applications at scale. We’re extremely happy with what we have been able to accomplish in previous years.
Qovery revival: Brand New Web Console for a world new Developer Experience
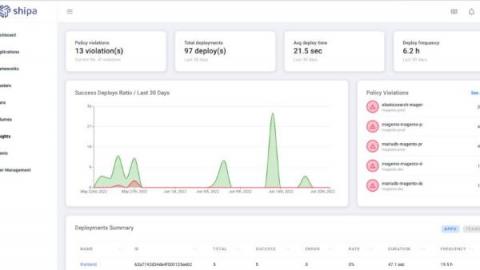
Are your applications secure? Can you find it out without complex rules?
The modernization of infrastructure and applications is driving the rapid growth of containers, and as companies scale the adoption of Kubernetes, it’s critical to incorporate security and compliance. The challenge? Compliance and security is a journey, not a state in time, and application security in Kubernetes has a large surface area. This challenge increases exponentially as you run more applications, onboard more developers, add more environments, add new pipelines, and more.