Operations | Monitoring | ITSM | DevOps | Cloud
Logging
The latest News and Information on Log Management, Log Analytics and related technologies.
What Is Operational Analytics? A Practical Introductory Guide
Cloud computing, mobile devices, and IoT technologies continue to evolve and proliferate. As a result, businesses are generating and collecting more data than ever before. Data is generated and stored every time a customer interacts with a website or device. Savvy companies understand the importance of capitalizing on that data. It enables them to enhance customer experiences and increase profitability, among other countless benefits.
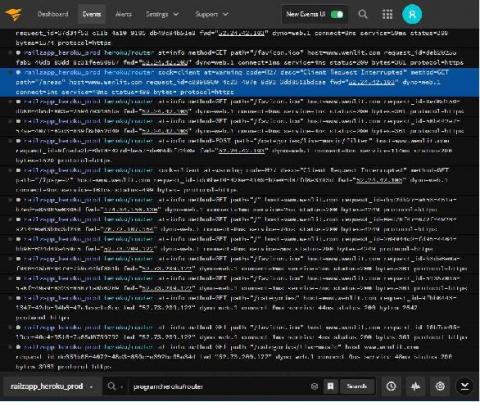
SolarWinds Papertrail Event Viewer Upgrade
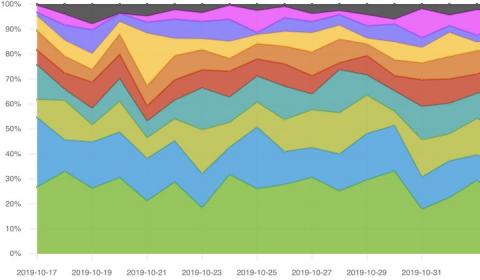
How to display data as a percentage in Kibana visualizations
Using percentages when performing data analytics is an essential approach to effective numeric comparison, especially when the data in question demonstrates drastically different sample sizes or totals. Percentages allow for a quick and accurate understanding of how much data sums have changed across a dimensional category like a range of time, geographic regions, product lines, etc.
Ransomware testing with Elastic Endpoint Security
As attackers continue to evolve and advance their techniques, tactics, and procedures (TTPs), it is crucial for enterprise organizations to deploy necessary countermeasures and defenses to secure their networks. Elastic Security provides an endpoint protection platform (EPP) with some of the most advanced and effective endpoint protections and preventions on the market today.
Using Logz.io for Spring Boot Logs
We recently wrote a blog with Julien Dubois, a Java Developer Advocate from Microsoft, on how to simplify logging for Spring Boot applications. This is a small preview. Spring Boot is an open source Java framework that makes it easier for developers to create microservices. Azure just announced Azure Spring Cloud, which will help Java engineers on Azure developer Java microservices faster. This blog explores how to simplify logging for Spring Boot applications.
Guide: RegEx 101 for Managing Log Data
Regular expressions can be crucial for wrangling log data efficiently. You may want to extract specific data from your logs to make it easier to analyze and visualize. Sometimes you might want to capture an email when a particular message is logged. Other times, you may find yourself needing to hide sensitive data in logs before they are saved. And more often than not, you need to match using a RegEx pattern rather than an exact text search. This guide is split into three parts.
2019 at a Glance: Logz.io Key Announcements
At AWS re:Invent recently, we excitedly announced Logz.io Infrastructure Monitoring – our new Grafana-based monitoring product! This product is the third pillar of our cloud observability platform, together with Logz.io Log Management and Logz.io Cloud SIEM.
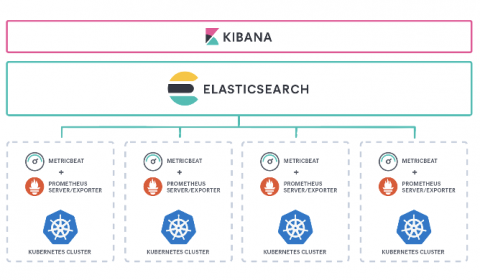
Prometheus monitoring at scale with the Elastic Stack
Tools. As engineers we all love great tools that help our teams work productively, resolve problems faster, be better. But tools can tend to grow in number, require additional maintenance, and most importantly, create silos. Each team has certain responsibilities and is constantly searching for tools that can address specific requirements in the best possible way.
Strengthening cybersecurity with log forensic analysis
Any system connected to the Internet is vulnerable to malicious attacks and breaches. If it’s online, there’s someone out there trying to break into it and do something bad with it (usually stealing data). Plain and simple. To protect your most valuable assets, you need bulletproof security measures, a skilled SecOps team, robust investigation tools, and reliable prevention/mitigation strategies.