Operations | Monitoring | ITSM | DevOps | Cloud
Logging
The latest News and Information on Log Management, Log Analytics and related technologies.
A tour of Go concurrency patterns via the new Heartbeat scheduler
Curious about how to write more idiomatic concurrent code in Go? It’s not always easy or intuitive, even if you’ve done lots of concurrent programming in other languages. I’ve been lucky to have worked in a well-written code base, and had the expert advice of Beats core area lead Steffen Siering along the way. In this post I’ll walk you through how we implemented a new scheduler for Heartbeat that is part of our upcoming 7.6.0 release.
How KeyBank used the Elastic Stack to build an enterprise monitoring solution
KeyBank is one of the largest banks in the United States. And as the bank has grown, so has their end-to-end monitoring system. With more than 1,100 branches and 1,400 ATMs stretching across 15 states, KeyBank’s infrastructure had evolved into a “Noah’s Ark of design,” says Mick Miller, Senior Product Manager, Cloud Native at KeyBank. In other words, they had two of everything, resulting in 21 different data islands.
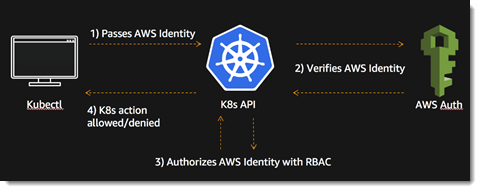
What is Amazon Elastic Kubernetes Service (EKS)?
Mac system extensions for threat detection: Part 1
When it comes to having visibility and detecting threats on macOS, one of the best sources of information for file system events, process events, and network events is the kernel. MacOS kernel extensions provide the ability to receive data about these events in real time with great detail. This is good for providing quick visibility into detecting anomalies and identifying possible threats.
How to Set Up Graylog GeoIP Configuration
Gathering logs that contain IP addresses are quite common across your infrastructure. Your firewalls, web servers, wireless infrastructure and endpoints can contain IP addresses outside your organization. Having additional data on those logs that gives you the Geolocation of the IP address helps in your investigations and understanding of your traffic patterns. For Example, if you can see logs on a World Map, you know if you are communicating to a country you don’t normally talk to.
Generate metrics from your logs to view historical trends and track SLOs
Web server logs and other access logs from technologies such as NGINX, Apache, and AWS Elastic Load Balancing (ELB) provide a wealth of key performance indicators (KPIs) for monitoring the health and performance of your application and understanding your users’ experience. These logs tell you how long pages take to load, where errors are occurring, which parts of your application are requested the most, and much more.
A Guide to 2020's Best Tech Events
2020 is finally here — and with the dawn of this new decade comes cutting-edge advancements to our platform as well as more opportunities to meet up and receive feedback from customers and community members at events around the world.
Log Forensics: The Basics of Finding Intel in Your Logs
Today’s post covers yet another log-related concept: log forensics. What’s this, and why should your organization care about it? Well, this is a topic related to logs, which are ubiquitous in the technology field. An IT organization that doesn’t generate many MBs worth of logs each day would be a rare occurrence nowadays. Even though logs are omnipresent, specific terms might not be so well-known. Not long ago, we covered log analytics, and today it’s log forensics time.
What Are the Differences Between On-premises and Cloud-based Log Management?
Cloud computing has changed the way we think about software, and opened up many new possibilities in both business and software development. Log management tools have also been affected by this, which begs the question – what are the pros and cons of cloud log management when compared to on-premises solutions? There are several key things you should consider before opting for either one, so here is a brief overview of the most important aspects that will help you make an informed decision.