Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
EventSentry Troubleshooting: Managing Database Size
How to Remove Trojan Viruses and Prevent Them in the Future
As subtle as they are dangerous, Trojan horses (or just “Trojans”) masquerade as benign software only to unleash havoc once inside your computer. Despite their stealthy nature, there are specific strategies you can employ to safeguard your digital assets from these threats. Below, we’ll discuss how to recognize the signs of a Trojan infection, steps for removing Trojan viruses from your devices, and how to reduce the risk of future infiltrations.
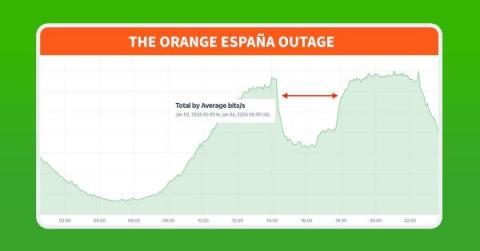
Digging into the Orange España Hack
Orange España, Spain’s second largest mobile operator, suffered a major outage on January 3, 2024. The outage was unprecedented due to the use of RPKI, a mechanism designed to protect internet routing security, as a tool for denial of service. In this post, we dig into the outage and the unique manipulation of RPKI.
Modernizing Financial Services with Automated, Proactive Threat Management
There’s a rising and intensifying pressure on financial services institutions that aligns with the demand for modernization, down to the core. It comes from laws like those of the Service Organization Control Type 2 (SOC 2) and the General Data Protection Regulation (GDRP), which enforce the need to build and hold down cybersecurity policies.
Navigating the Transition to Secure Texting
Recently, I stumbled upon an eye-opening NPR podcast that delved into the lingering use of pagers in healthcare—a seemingly outdated technology that continues to drive communication in hospitals. As I listened through the debate around its persistence, discussing challenges and unexpected benefits, it prompted reflections on facilitating a seamless shift to secure phone-app-based texting, acknowledging the considerable advantages it brings.
Exoprise Completes SOC 2 Type II Audit
Navigating Healthcare Maze With Transcription Services: Utilizing Transcription Services Effectively
Comodo SSL Certificate: Your Complete Guide to Trusted Web Security
CFEngine 2023 retrospective
As we bid farewell to 2023, it’s once again time to reflect on the milestones and progress we’ve made throughout the year. This year is especially significant because it marks 30 years since CFEngine’s birth. From its humble beginnings at the University of Oslo to the thousands of implementations across the world and counting, CFEngine has not only weathered the twists and turns of life, but has thrived in an industry where many have come and gone.