Operations | Monitoring | ITSM | DevOps | Cloud
Security
The latest News and Information on CyberSecurity for Applications, Services and Infrastructure, and related technologies.
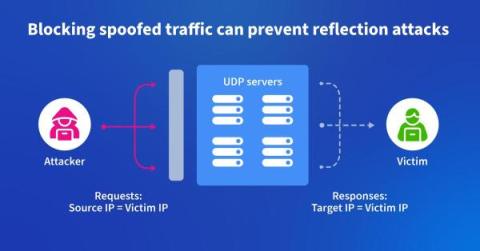
Using Kentik to Fight DDoS at the Source
In this blog post, we describe how one backbone service provider uses Kentik to identify and root out spoofed traffic used to launch DDoS attacks. It’s a “moral responsibility,” says their chief architect.
AWS KMS Use Cases, Features and Alternatives
A Key Management Service (KMS) is used to create and manage cryptographic keys and control their usage across various platforms and applications. If you are an AWS user, you must have heard of or used its managed Key Management Service called AWS KMS. This service allows users to manage keys across AWS services and hosted applications in a secure way.
How Shopify Can Jumpstart Your eCommerce Business
Redefining Financial Services with On-Demand Virtual Servers
Service Evolution In The Digital Age: Business Practices Worth Considering
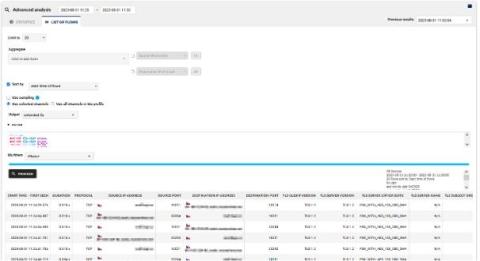
Monitoring TLS Network Traffic for Non-FIPS Compliant Cipher Suites
FIPS compliant cipher suites hold the U.S. government's seal of approval, guaranteeing their suitability for federal systems. On the other hand, non-FIPS compliant cipher suites may present security vulnerabilities due to outdated cryptographic algorithms and potential lack of perfect forward secrecy. As a result, it becomes paramount to monitor TLS network traffic for non-FIPS compliant cipher suites.